
Learn what code signing is, how it works, and why enterprises rely on it to secure software, CI/CD pipelines, and trust.
Introduction
Modern software moves fast. Code is written, built, shipped, patched, and redeployed continuously across cloud platforms, endpoints, containers, and devices. In this environment, trust is no longer assumed — it must be proven every time software runs.
Code signing is one of the most critical trust mechanisms in modern cybersecurity. It ensures that software has not been tampered with and that it originates from a verified, trusted publisher. Without it, enterprises expose themselves to malware injection, supply chain attacks, and silent compromise.
This guide explains code signing from first principles to enterprise-scale implementation, with practical insights for security, DevOps, and compliance teams.
What This Guide Covers
- What code signing is and how it works
- Why code signing matters in modern enterprises
- Technical mechanics of digital signatures
- Enterprise code signing architecture workflows
- Best practices for secure implementation
- Common pitfalls and how to avoid them
- Advanced and cloud-native use cases
- How QCecuring compares to industry alternatives
Workflow Diagram Overview
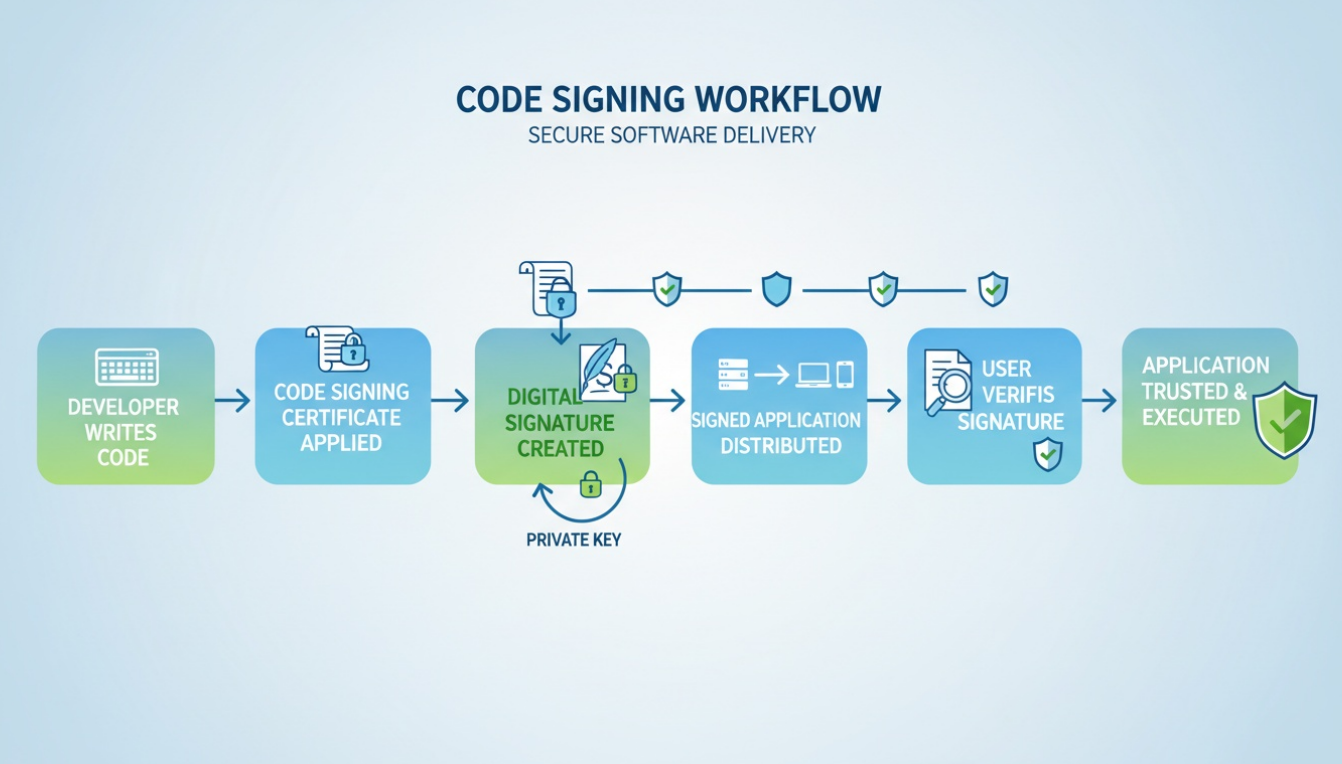
At a high level, code signing embeds a cryptographic signature into software during the build or release process. When that software runs, operating systems, platforms, or security tools verify the signature before allowing execution.
This verification step is what establishes trust — and what blocks unauthorized or malicious code.
1. What Is Code Signing?
Code signing is the process of digitally signing software, scripts, or binaries using cryptographic keys to prove authenticity and integrity.
When software is signed:
- The publisher’s identity is cryptographically bound to the code
- Any post-signing modification invalidates the signature
- Systems can automatically verify trust before execution
Code signing is used across operating systems, cloud platforms, mobile ecosystems, and embedded devices. It is foundational to secure software delivery.
At its core, code signing solves three problems:
- Authenticity — Who created this software?
- Integrity — Has it been altered since signing?
- Trust — Should this software be allowed to run?
2. Why Code Signing Matters Today
Software supply chain attacks have shifted the threat landscape. Attackers no longer need to breach production systems directly — they inject malicious code earlier in the pipeline.
Code signing directly mitigates this risk.
In modern environments, code signing supports:
- Cloud-native CI/CD pipelines
- Zero Trust execution models
- Regulatory and compliance mandates
- Platform enforcement by Windows, macOS, mobile OSs, and cloud runtimes
Unsigned or improperly signed code increasingly fails to run at all. For enterprises, this makes code signing not optional, but mandatory.
3. How Code Signing Works
Code signing relies on public key cryptography and digital certificates.
The simplified flow looks like this:
Source Code
→ Build System compiles artifact
→ Hash generated from binary
→ Signing Service receives hash
→ Private key signs hash
→ Digital signature created
→ Signature embedded into artifact
→ Signed software published
→ Runtime loads software
→ Signature extracted
→ Hash recomputed
→ Public key verifies signature
→ Trust validated
→ Execution allowedWhen a system verifies signed code, it:
- Extracts the signature
- Recomputes the hash of the code
- Validates the signature using the public key
- Confirms certificate trust and validity
If any step fails, execution is blocked or flagged.
Technical ASCII diagram of Code Signing process:
4. Architecture Workflow
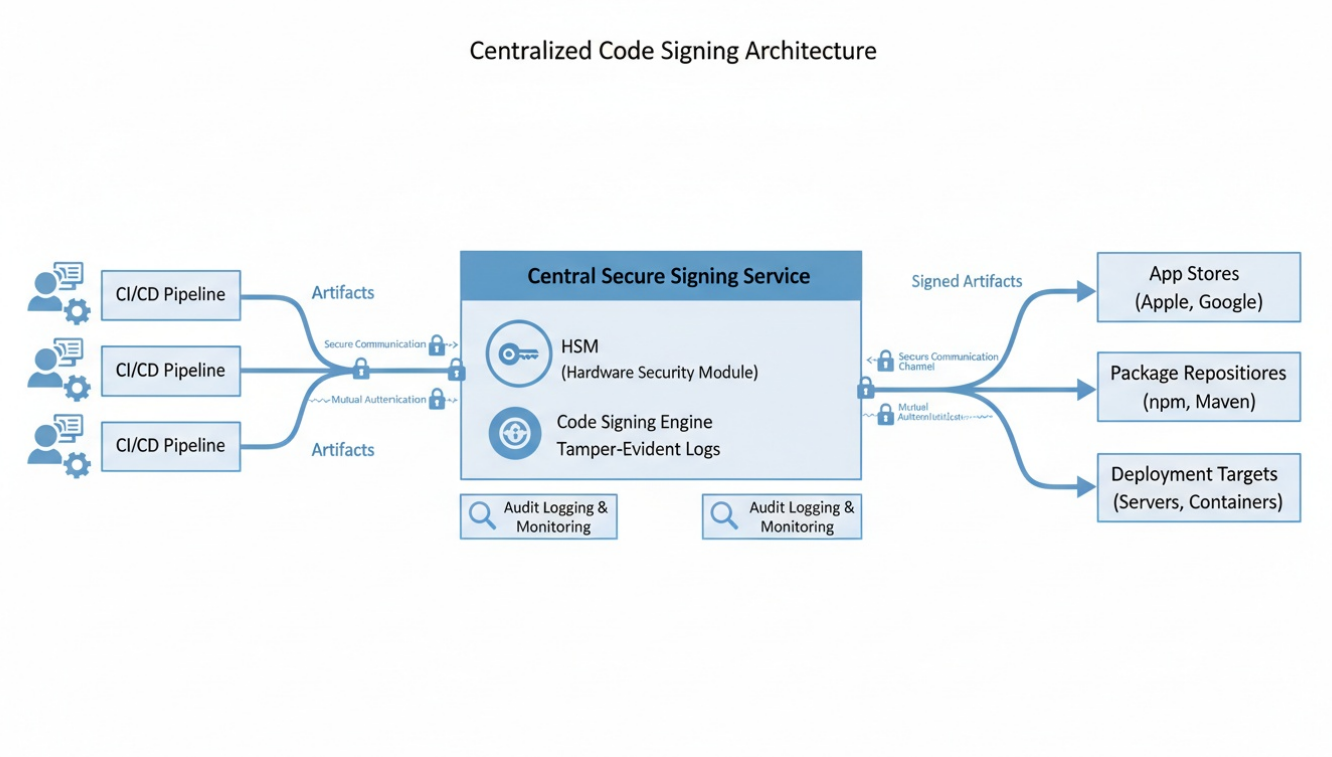
In enterprise environments, code signing must be centralized, auditable, and automated.
A typical workflow includes:
- Developers push code to source control
- CI pipelines trigger builds
- Signing requests are sent to a centralized signing service
- Private keys are protected by HSMs or cloud key management
- Signed artifacts are stored and distributed
This architecture ensures keys are never exposed to developers or build agents directly.
5. Real Code Snippets
Signing a Binary with OpenSSL
openssl dgst -sha256 -sign private.key -out signature.bin app.binVerifying a Signature
openssl dgst -sha256 -verify public.key -signature signature.bin app.binCI Pipeline Signing Step
steps:
- name: Sign Artifact
run: qcecuring sign --artifact build/app.bin6. Best Practices
- Use centralized signing services
- Protect private keys with HSMs
- Enforce role-based access controls
- Automate signing in CI/CD pipelines
- Rotate signing certificates regularly
- Separate development and production keys
- Log and audit all signing events
- Enforce policy-based approvals
- Integrate with identity providers
- Validate signatures at runtime
- Monitor certificate expiration
- Use timestamping services
- Avoid local developer signing keys
7. Common Pitfalls
- Hardcoding private keys in pipelines
- Sharing signing certificates across teams
- Manual signing processes
- Missing audit trails
- Expired certificates breaking releases
- Inconsistent signing policies
- Lack of revocation planning
These issues often surface only during incidents — when it is already too late.
8. Advanced Use Cases
Modern enterprises extend code signing beyond traditional binaries.
Advanced scenarios include:
- Signing container images
- Securing Kubernetes admission controls
- Enforcing signed Terraform and IaC templates
- Mobile application signing
- Firmware and IoT device signing
- Zero Trust workload execution
As environments become more distributed, code signing becomes a universal trust signal.
Competitor Comparison
| Capability | QCecuring | DigiCert | Venafi | Keyfactor | Encryption Consulting |
|---|---|---|---|---|---|
| Centralized Signing | Yes | Yes | Yes | Yes | Limited |
| CI/CD Automation | Native | Partial | Partial | Partial | No |
| HSM Integration | Native | Yes | Yes | Yes | Yes |
| Policy Enforcement | Advanced | Basic | Advanced | Advanced | Basic |
| Enterprise Scale | High | High | High | High | Medium |
QCecuring focuses on automation-first, enterprise-grade code signing built for modern pipelines.
Keyword Expansion Zone
- enterprise code signing solutions
- software supply chain security
- secure CI/CD pipelines
- digital signature verification
- signed software execution
- code signing certificates
- DevSecOps signing automation
External Resources
- NIST SP 800-161: Supply Chain Risk Management
- CISA: Securing the Software Supply Chain
- CA/Browser Forum: Code Signing Requirements
Final Summary
- Code signing establishes software trust
- It prevents tampering and impersonation
- Automation is critical at scale
- Centralized key protection is essential
- Modern enterprises cannot operate without it
FAQs
Q: What happens if signed code is modified? The signature becomes invalid and execution fails.
Q: Is code signing required for cloud workloads? Increasingly yes, especially in Zero Trust environments.
Q: Can code signing be automated? Yes, and it should be for enterprise scale.
Q: Are HSMs mandatory? Strongly recommended for private key protection.
Q: Does code signing stop malware? It prevents unauthorized code from executing.
Q: Is code signing only for binaries? No, scripts, containers, and firmware can all be signed.
Ready to Secure Your Enterprise?
Discover how QCecuring can help you automate certificate lifecycle management, secure SSH keys, and protect your cryptographic infrastructure.



