
Understanding the cryptographic process that unlocks secure data for authorized users
Introduction
In our increasingly digital world, protecting sensitive information has become paramount for individuals and organizations alike. While encryption transforms readable data into an unreadable format, decryption reverses this process — turning scrambled data back into its original, understandable form.
Whether you’re securing personal emails, protecting corporate databases, or safeguarding government communications, understanding decryption is essential for maintaining data confidentiality, ensuring secure communications, complying with privacy regulations, and building robust cybersecurity frameworks.
The balance between keeping data secure and making it accessible to authorized users lies at the heart of effective decryption strategies. This process requires careful key management, robust algorithms, and secure implementation practices.
What This Guide Covers
- What is decryption and how it works
- Core components of decryption systems
- Symmetric vs asymmetric decryption
- Enterprise use cases
- Security best practices
- Common challenges and solutions
- Emerging trends in decryption technology
- Competitor landscape comparison
Workflow Diagram Overview
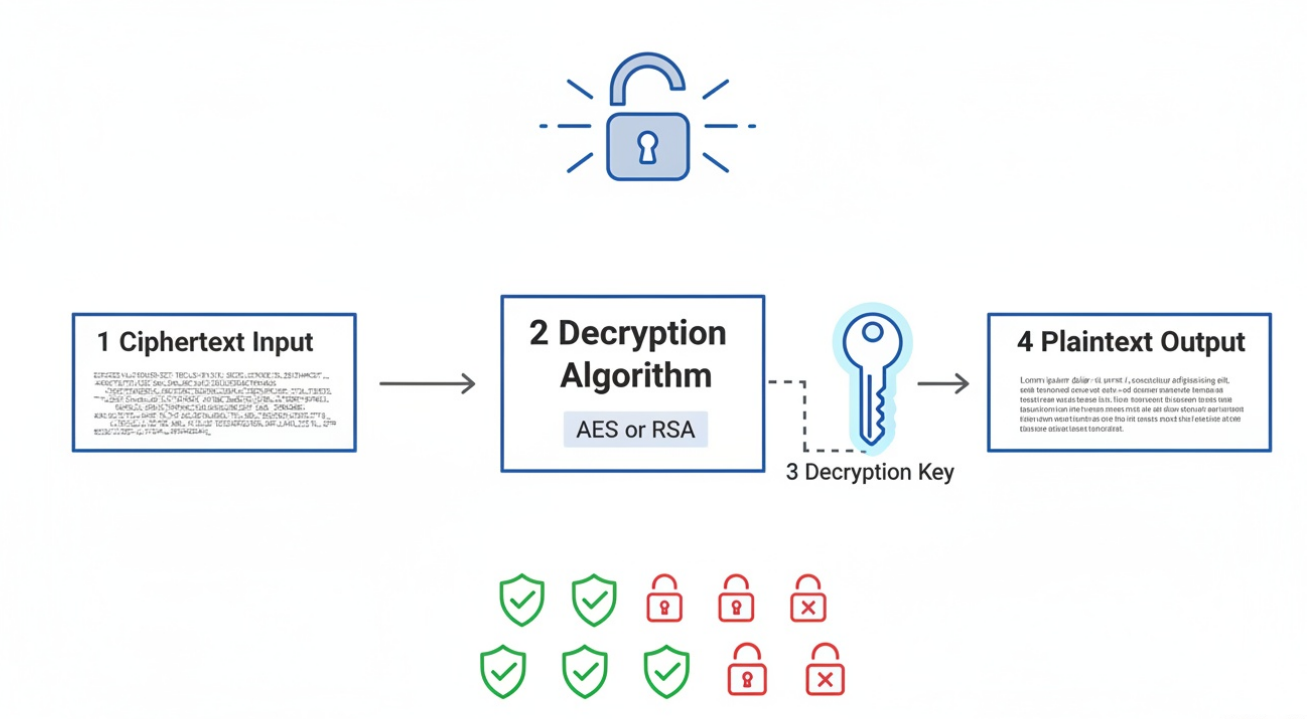
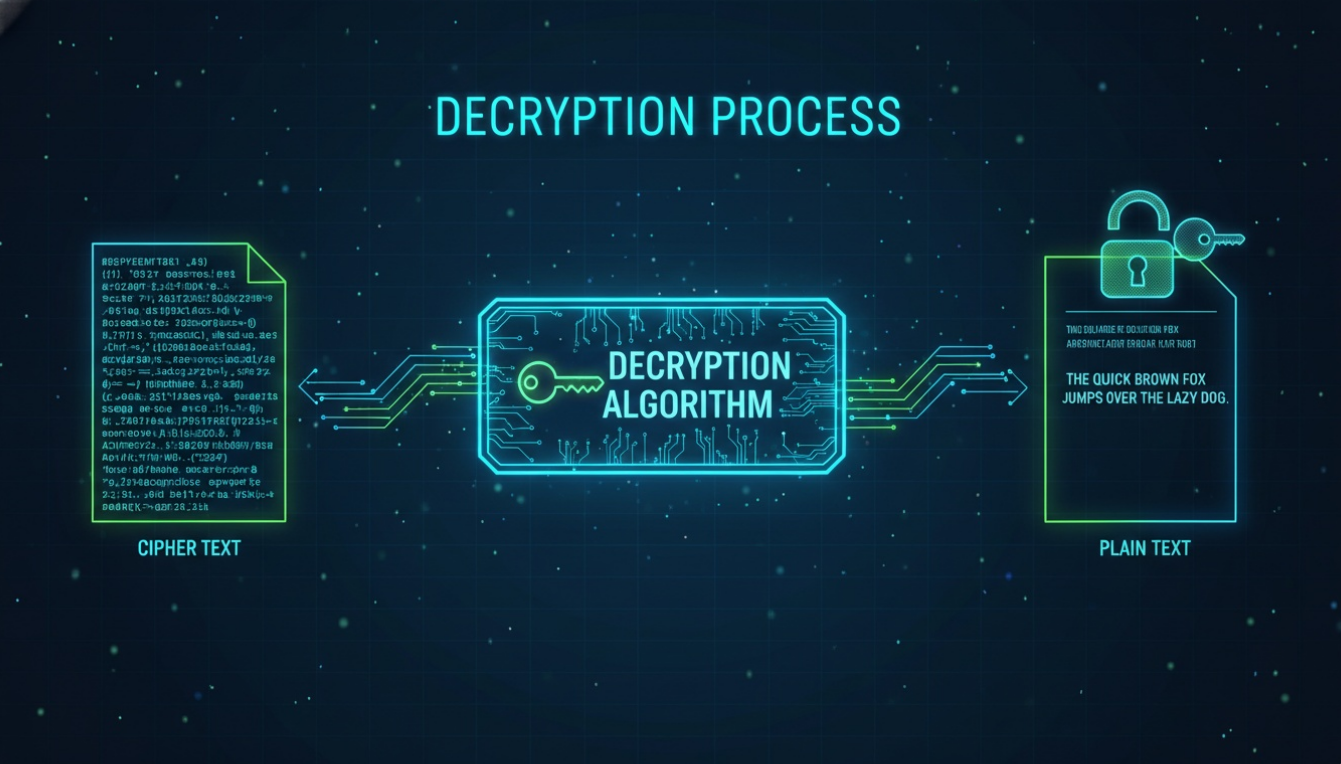
This flow shows how encrypted data is transformed back to readable format through the application of decryption keys and algorithms.
1. What Is Decryption?
Decryption is the cryptographic process of converting encrypted (ciphered) data back into its original, readable format using a specific key or algorithm.
Explain using bullets:
- What decryption is - The reverse process of encryption that unlocks secure data
- What problem it solves - Makes encrypted data accessible to authorized users
- Where it is used - Everywhere encrypted data needs to be accessed
- Who needs it - Anyone who uses encrypted communications or storage
2. Why Decryption Matters Today
- Cybersecurity - Essential for protecting and accessing sensitive data
- Cloud-native architectures - Required for accessing encrypted cloud storage
- Identity & access - Critical component of authentication and authorization
- Enterprise compliance - Necessary for meeting data protection regulations
- Zero trust - Enables secure access to encrypted resources
- Scalability - Must work efficiently at enterprise scale
- Data recovery - Critical for business continuity when encrypted backups need restoration
Authoritative sources for further reading:
3. Technical Deep Dive
Use nested bullet points + short paragraphs.
-
Symmetric Decryption
- Uses the same key for encryption and decryption
- Faster processing speeds
- Examples: AES, DES, 3DES
- Requires secure key distribution mechanisms
-
Asymmetric Decryption
- Uses a pair of keys (public and private)
- More secure key distribution
- Examples: RSA, ECC, ElGamal
- Private key decrypts data encrypted with public key
Technical ASCII diagram of decryption process:
Encrypted Data Decryption Key
| |
| Decryption Algorithm |
| (AES, RSA, etc.) |
v v
+---------+ +---------+
| Cipher | | Key |
| Text |--------------------->| Storage |
+---------+ +---------+
|
| Decryption Process
v
+---------+
| Plain |
| Text |
+---------+
|
v
Authorized Access4. Architecture Workflow
Describe the full flow in clear numbered steps.
- Encrypted data (cipher text) is received by the system
- System identifies required decryption key from secure storage
- Appropriate decryption algorithm is selected based on encryption method
- Key is applied to cipher text using the decryption algorithm
- Plain text is produced and validated for integrity
- Decrypted data is made available to authorized users with proper access controls
- Operation is logged for audit and compliance purposes
5. Real Code Snippets
Provide 2–5 code blocks, depending on topic.
OpenSSL Decryption Example
openssl enc -d -aes-256-cbc -in encrypted.file -out decrypted.filePython Decryption Example
from cryptography.fernet import Fernet
cipher_suite = Fernet(key)
decrypted_text = cipher_suite.decrypt(encrypted_text)
print(decrypted_text.decode())Node.js Decryption Example
const crypto = require('crypto');
const decipher = crypto.createDecipher('aes-256-cbc', key);
let decrypted = decipher.update(encrypted, 'hex', 'utf8');
decrypted += decipher.final('utf8');
console.log(decrypted);Java Decryption Example
import javax.crypto.Cipher;
import javax.crypto.spec.SecretKeySpec;
import java.util.Base64;
public class DecryptionExample {
public static String decrypt(String encryptedData, String key) throws Exception {
SecretKeySpec secretKey = new SecretKeySpec(key.getBytes(), "AES");
Cipher cipher = Cipher.getInstance("AES");
cipher.init(Cipher.DECRYPT_MODE, secretKey);
return new String(cipher.doFinal(Base64.getDecoder().decode(encryptedData)));
}
}6. Best Practices
Use a clean bullet list:
- Store decryption keys securely in hardware security modules (HSMs)
- Implement proper access controls with role-based permissions
- Regularly rotate encryption keys to minimize exposure risk
- Use hardware security modules (HSMs) for key storage and processing
- Monitor decryption attempts for suspicious activity patterns
- Maintain algorithm updates to address known vulnerabilities
- Document key recovery procedures for disaster scenarios
- Train personnel on secure key handling and management
- Validate decrypted data integrity using checksums or hashes
- Log all decryption operations for audit trail compliance
- Encrypt data in transit during decryption processes
- Implement key backup and recovery procedures
- Use strong key generation methods with sufficient entropy
- Segregate decryption environments from other system components
- Audit decryption processes regularly for compliance gaps
7. Common Pitfalls
Examples:
- Storing decryption keys insecurely in plain text files
- Using weak or outdated algorithms like DES or RC4
- Failing to rotate keys regularly leading to key compromise
- Not validating decrypted data integrity causing corruption issues
- Inadequate access controls allowing unauthorized decryption
- Poor key management practices resulting in lost keys
- Ignoring decryption logging and monitoring capabilities
- Using the same key for multiple unrelated purposes
- Hardcoding keys in application source code
- Neglecting to securely erase decrypted temporary files
8. Advanced Use Cases
Include:
- Cloud-native automation - Automated decryption in cloud environments with key management services
- Enterprise IAM alignment - Integrating decryption with identity management for contextual access
- CI/CD integration - Securing pipeline data with decryption during build processes
- IoT enrollment at scale - Managing decryption for IoT device communications with constrained resources
- Container security workflows - Protecting containerized applications with decryption at runtime
- Zero-trust network access - Decrypting traffic only after verifying endpoint compliance
- Multi-cloud key federation - Unified decryption across AWS, Azure, and Google Cloud platforms
Competitor Comparison
How QCecuring stacks up against major competitors in decryption capabilities:
| Feature | QCecuring | DigiCert | Venafi | Keyfactor | Encryption Consulting |
|---|---|---|---|---|---|
| Automated Key Rotation | Advanced | Basic | Good | Comprehensive | Manual |
| HSM Integration | Native | Partial | Full | Enterprise | Limited |
| Cloud Platform Support | All Major | Select | Broad | Extensive | Few |
| Zero Trust Alignment | Built-in | Add-on | Integrated | Framework | Custom |
| API-First Architecture | Yes | Limited | Yes | Yes | Legacy |
| Real-time Monitoring | Continuous | Scheduled | Near-real | Live | Batch |
Keyword Expansion Zone
Writers MUST integrate SEMrush additional keywords naturally here.
- What is decryption process and how it ensures data security
- Symmetric decryption techniques for high-speed data processing
- Asymmetric decryption methods for secure key exchange
- Cipher text conversion back to readable format
- Decryption key management in enterprise environments
- Encryption vs decryption comparison for security teams
- Data decryption best practices for compliance
- Secure data decryption workflows in hybrid cloud
- Hardware security modules for decryption key storage
- Decryption algorithms performance benchmarks
External Resources
- NIST Cryptographic Standards
- ISO/IEC 27001 Standards
- Wikipedia: Decryption
- Cloudflare: Encryption Concepts
- Microsoft Security Documentation
Final Summary
- Decryption converts encrypted data back to readable format using cryptographic keys
- Symmetric decryption uses the same key for encryption and decryption processes
- Asymmetric decryption uses a private key to decrypt data encrypted with a public key
- Proper key management is critical for successful and secure decryption operations
- Decryption is essential for accessing protected data while maintaining security posture
FAQs
Q: What is the difference between encryption and decryption? A: Encryption converts readable data into an unreadable format to protect it, while decryption reverses this process to make the data readable again. Both are complementary cryptographic processes.
Q: What are the two main types of decryption? A: The two main types are symmetric decryption (using the same key for encryption and decryption) and asymmetric decryption (using a private key to decrypt data encrypted with a corresponding public key).
Q: Is decryption legal? A: Yes, decryption is legal when performed by authorized parties with proper access rights. Unauthorized decryption of data you don’t own or have permission to access may violate laws.
Q: What happens if you lose a decryption key? A: If you lose a decryption key, you typically cannot access the encrypted data. This is why proper key management, backup, and recovery procedures are essential for any encryption system.
Q: How does quantum computing affect decryption? A: Quantum computers could potentially break current asymmetric encryption methods, requiring new quantum-resistant algorithms. However, symmetric encryption with sufficiently long keys would remain secure with doubled key lengths.
Q: Can encrypted data be decrypted without a key? A: In theory, yes, through brute force attacks, but this is computationally impractical with modern encryption standards. Properly implemented encryption with strong keys remains secure against unauthorized decryption attempts.
Q: What is the role of a Hardware Security Module (HSM) in decryption? A: An HSM securely generates, stores, and manages cryptographic keys, performing decryption operations within a tamper-resistant environment to prevent key exposure and unauthorized access.
Ready to Secure Your Enterprise?
Discover how QCecuring can help you automate certificate lifecycle management, secure SSH keys, and protect your cryptographic infrastructure.



